在2016年12月14日,Docker 公司宣布将containerd 从 Docker 中分离,由开源社区独立发展和运营。Containerd 完全可以单独运行并管理容器,而 Containerd 的主要职责是镜像管理和容器执行。同时,Containerd 提供了 containerd-shim 接口封装层,
向下继续对接 runC 项目,使得容器引擎 Docker Daemon 可以独立升级。
Containerd 可以在宿主机中管理完整的容器生命周期:容器镜像的传输和存储、容器的执行和管理、存储和网络等。总结一下,它主要负责干以下事情:
管理容器的生命周期(从创建容器到销毁容器) 拉取/推送容器镜像 存储管理(管理镜像及容器数据的存储) 调用 runC 运行容器(与 runC 等容器运行时交互) 管理容器网络接口及网络
containerd的安装方法
yum install -y yum-utils device-mapper-persistent-data lvm2 yum-config-manager --add-repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo sed -i 's+download.docker.com+mirrors.aliyun.com/docker-ce+' /etc/yum.repos.d/docker-ce.repo yum makecache fast yum install containerd -y containerd --version
启动containerd并添加开机启动
systemctl start containerd systemctl enable containerd systemctl status containerd
contianerd配置文件
containerd config default > /etc/containerd/config.toml
然后保存重启containerd
systemctl restart containerd
下面介绍一些containerd常用命令
介绍使用命令之前先介绍下ctr和crictl命令和区别
ctr是containerd本身的CLI,crictl是Kubernetes社区定义的专门CLI工具
ctr images list #查看本地镜像 ctr images ls #查看导入的镜像 ctr images pull 192.168.1.72:5000/test/alping:v1 --skip-verify --user=admin:admin123 #拉取镜像,如果仓库是http协议地址,需要添加--plain-http参数 ctr images push 192.168.1.72:5000/test/alping:v1 --skip-verify --user=admin:admin123 #推送镜像 ctr images tag docker.io/docker/alpine:latest 192.168.1.72:5000/test/alping:v1 #改标签,images可以简写成i ctr images import alping_v1.tar #导入镜像 ctr images export alping_v1.tar 192.168.1.72:5000/test/alping:v1 #导出镜像 ctr i ls -q #镜像列表 ctr i rm 192.168.1.72:5000/test/alping:v1 #删除镜像 ctr ns ls #查看命名空间 ctr c ls #查看停止的容器 ctr c rm test-v1 #删除停止的容器
启动容器
ctr -n k8s.io run 192.168.1.2/orionx/native:tensorflow2.4.1-hvd0.21.3-cu11.1-cudnn8-py3.6-ubuntu18.04 benchmark
benchamrk是启动的容器名字,如果需要启动到后台需要增加--detach/-t参数,添加一个伪终端加-t参数
以下是一个完成的启动示例
ctr -n k8s.io run -d -t \ --env ORION_GMEM=6000 \ --env ORION_RATIO=50 \ --env ORION_VGPU=1 \ --env ORION_CROSS_NODE=0 \ --env ORION_DEVICE_ENABLE=1 \ --env ORION_DRIVER_ONLY=true \ --env ORION_SIM_NVSMI_FORCE=1 \ --env ORION_EXPORT_CMD="env |grep ORION; orion-smi -j" \ 192.168.1.2/orionx/native:tensorflow2.4.1-hvd0.21.3-cu11.1-cudnn8-py3.6-ubuntu18.04 \ benchmark2
可以通过ctr命令继续查看容器
ctr -n k8s.io task ls
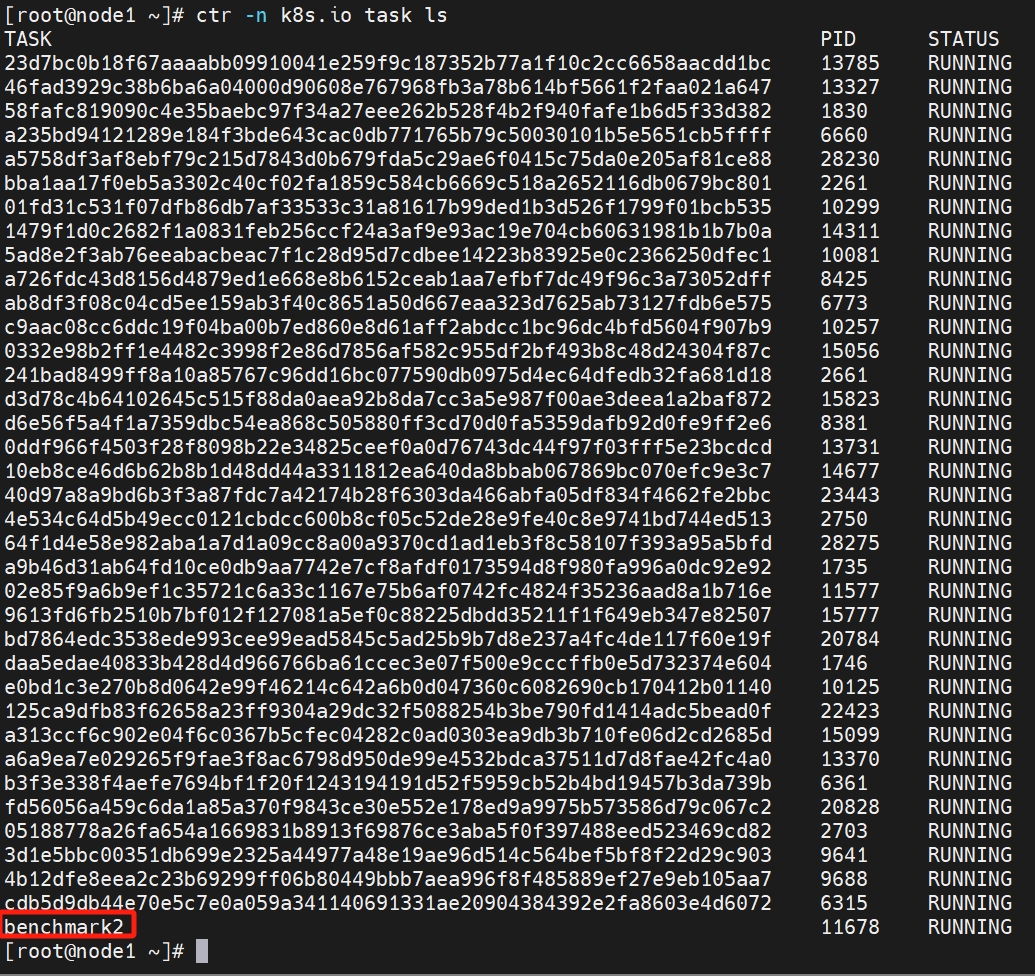
可以通过exec命令进入容器内
ctr -n k8s.io task exec -t --exec-id 11678 benchmark2 bash
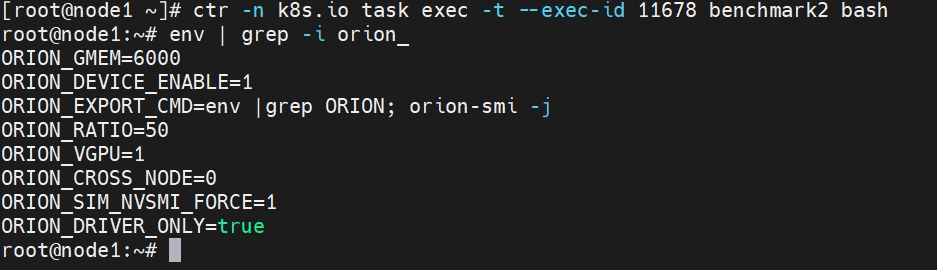
可以看到我们刚才配置的环境变量都在注入在容器内部了。
接着来我们看看删除容器部分命令操作,分为两部
需要先停止容器才能再做删除操作
ctr -n k8s.io task kill -s 9 benchmark2 #停止容器 ctr -n k8s.io c rm benchmark2 #删除容器 ctr -n k8s.io c ls #可以查看容器,如果列表里面没有就是被删除
如果需要挂载文件目录可以使用--mount参数,src是本机目录或文件,dst是容器内目录或文件,options是操作权限,有只读ro,读写rw
--mount type=bind,src=/etc/localtime,dst=/etc/localtime,options=rbind:ro
还可以添加--runtime指定runtime,默认是config.toml文件里面指定的,我们也可以直接指定"io.containerd.runc.v2"
ctr -n k8s.io run --runtime io.containerd.runtime.v1.linux 192.168.1.2/orionx/native:tensorflow2.4.1-hvd0.21.3-cu11.1-cudnn8-py3.6-ubuntu18.04 benchmark2
还可以添加--runc-binary参数指定runtime的二进制文件
ctr -n k8s.io run --runc-binary /usr/bin/nvidia-container-runtime 192.168.1.2/orionx/native:tensorflow2.4.1-hvd0.21.3-cu11.1-cudnn8-py3.6-ubuntu18.04 benchmark2
最后是containerd清理未使用镜像的命令
ctr -n k8s.io image prune --all 如果是crictl命令如下 crictl rmi --prune --all
再附上crictl一些常用命令
crictl ps #显示当前运行的容器列表 crictl images #查看镜像列表 crictl rmi #删除镜像 crictl rm #删除一个容器 crictl stats #查看容器状态 crictl exec #进入容器内 crictl exec -it <container_id> bash crictl start/stop #启动和停止容器 crictl logs #查看容器日志 crictl pull #拉取镜像 crictl inspect #查看一个容器的状态信息 crictl inspecti #查看一个镜像的状态信息 crictl inspectp #查看一个POD的状态信息 crictl pods #列出pod列表
